Mr. J, a Former Professor Series – Entry 19: The Coward Behind the Clone
Recognizing the Signature – When Passive Aggression Isn’t So Subtle
When Accusations Miss the Address
Restacked from a public post. The respondent’s comment below was unsolicited and irrelevant, yet indicative of their ongoing pattern of inappropriate online behavior.
The original post was a public satire. His unsolicited comment below reveals a consistent lack of contextual awareness and impulse control.
Translation:
Subject: Report on Suspected Personal Income Tax Evasion
To: [Confidential] District Tax Department
I am writing this letter to report a case of suspected personal income tax evasion occurring within [District Name] area.
Details of the individual being reported:
Full name, date of birth, and address: withheld for confidentiality
Suspected conduct:
Over the past two years, the individual has been operating in the field of real estate marketing. However, there is no indication that she has declared or paid personal income tax in accordance with legal regulations.
Additionally, this person is reportedly involved in brokering and selling apartments or construction projects that do not comply with legal standards. This may pose risks to consumers and violate regulations on construction and housing law.
This behavior is particularly condemnable and shameful given that Ms. Linh’s father — a government official — is fully aware of the situation but has taken no action.
I am submitting this information in the hope that the competent authorities will conduct verification and take action if there are any violations of the law.
I am willing to provide further information if needed.
Screenshot captured on June 18, 2025; archived prior to deletion
The alleged contains language that violates ethical reporting norms — attempting to humiliate the complainant by targeting her family’s reputation, rather than presenting verifiable financial evidence. Such language undermines the credibility and admissibility of the complaint.
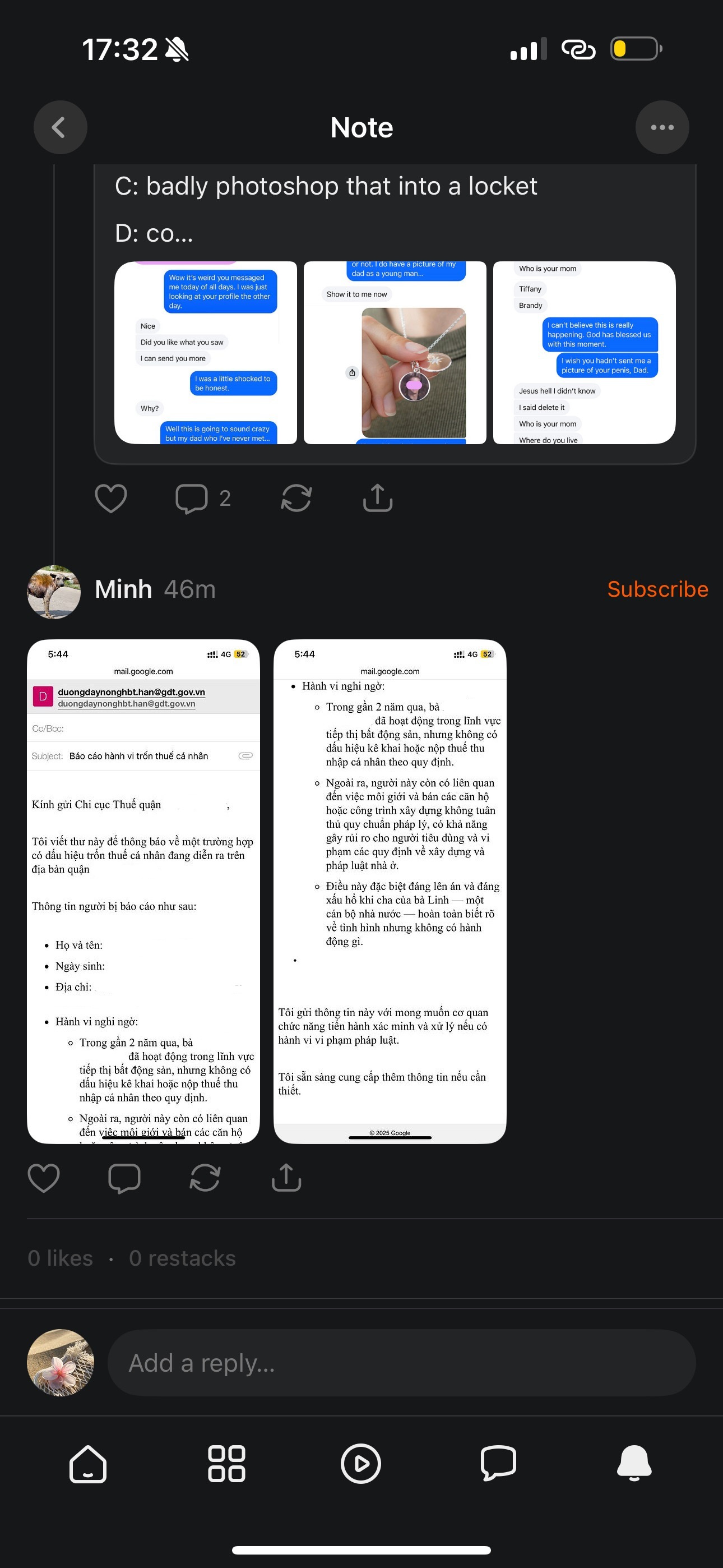
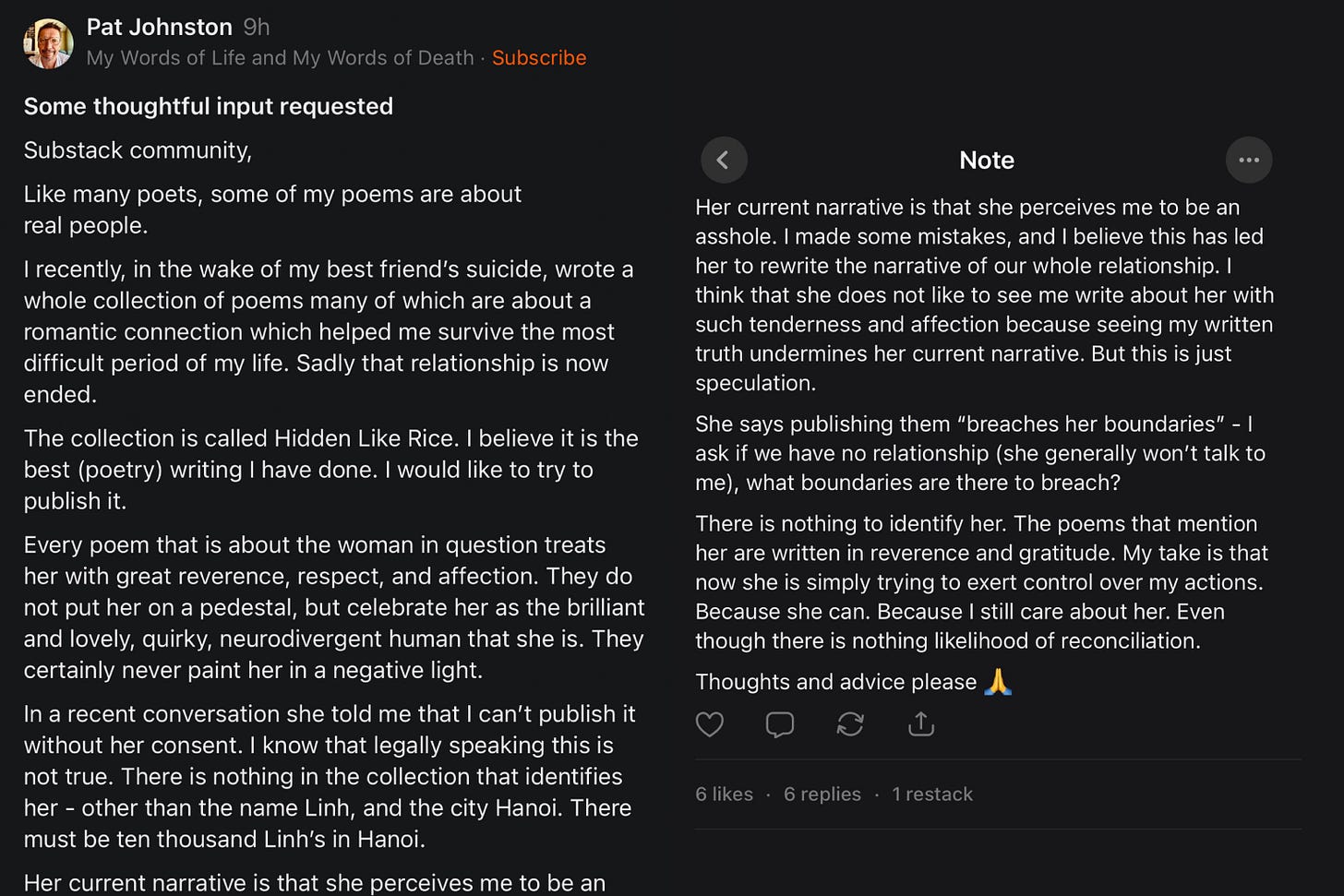
Some people seem to believe that simply typing a few lines in a comment box gives themselves the power to “expose” someone — no evidence, no verification, not even… the right address.
Recently, I was accused — quite publicly — of tax evasion by someone who couldn’t even get the district or street number right.
Even though I have no obligation to respond to unfounded claims from strangers with no authority.
But baseless accusations aren’t bravery.
They’re just a desperate way for someone irrelevant to feel like they still matter.
And slander, if it continues, can absolutely be responded to — legally.
The anonymous “tax evasion tip-off” was clumsy at best — the location was wrong, the allegations baseless, and the language? Far too familiar.
It didn’t take long for me to recognize the tone, the phrasing, the oddly specific way they referred to my address. Only one person — an older foreign man I used to know — ever referred to that block the way it appeared in the email. Locals wouldn’t phrase it that way. They just don’t.
Public Note published by Pat Johnston (captured June 19, 2025; archived prior to deletion)
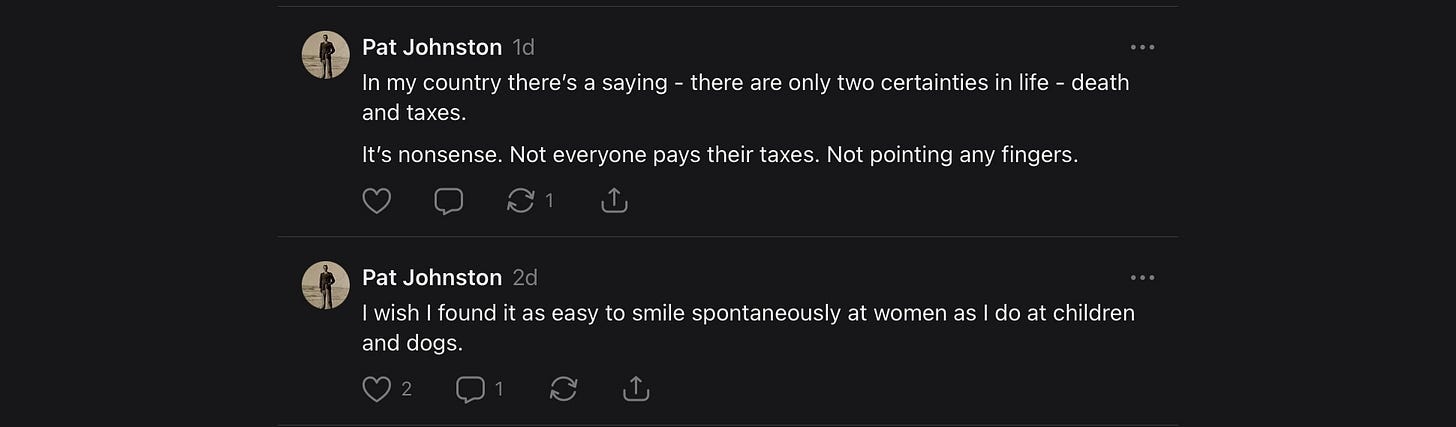
And this earlier post surfaced — one of many:
“Not everyone pays their taxes. Not pointing any fingers.”
(Followed by other threats I’ve already archived)
Read my related publication: Mr. J, a Former Professor Series – Entry 8: What Makes a Scholar Dangerous here.
The pattern is clear. The irony is clearer: the man making veiled accusations about taxes is the very one who once admitted to working illegally in Hong Kong, seeking sympathy while ducking accountability.
So if you’re wondering how I knew who sent it: it’s not because I’m guessing. It’s because people leave fingerprints in language. Especially when they think they’re being clever.
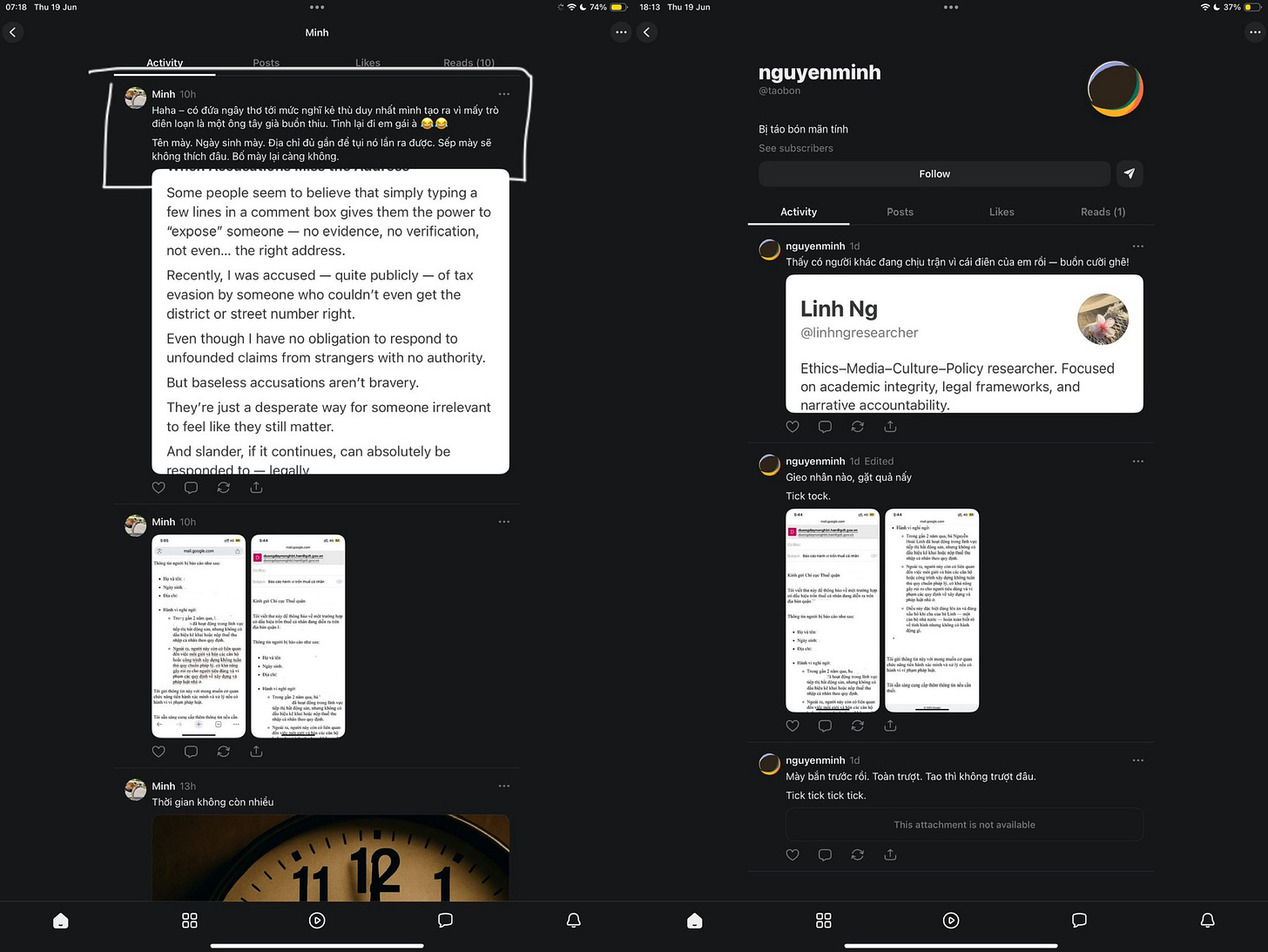
As of 18 June 2025, the Substack account “Minh” — which publicly posted defamatory claims and a fabricated email addressed to my country’s tax authorities — is being followed by Pat Johnston’s Substack account.
While this alone does not establish authorship, it raises serious concerns about tacit endorsement, coordination, or active surveillance of accounts engaged in reputational harassment.
This connection, combined with the tone and timing of Pat Johnston’s earlier post referencing “taxes,” warrants deeper scrutiny.
He denied any involvement in the anonymous smear.
And yet — there he was. Quietly following the very account that published it.
Silence isn’t neutrality. It’s strategy. Until it backfires.
Publishing someone’s face without consent — especially in the context of an anonymous attack — is not protected expression. It is harassment, a privacy violation, and in many jurisdictions, a prosecutable offence.
“Coincidence” isn’t a defense when your digital trace shows interest before denial.
Use of Clone Accounts for Tax Defamation and Public Threats
The deployment of anonymous or clone accounts to disseminate defamatory claims — including tax-related accusations and reputational threats — remains traceable via IP data if subjected to formal investigation.
Such actions may constitute serious breaches under laws governing:
Defamation and harassment
Unauthorized disclosure of personal information
Digital integrity and cyber safety regulations
Where linguistic patterns, behavioral timing, or account interactions suggest links to a known individual, the use of a clone account ceases to serve as a shield.
Instead, it becomes a strategic liability — a poorly disguised tool of evasion that may be treated as evidence of premeditated misconduct.
On Cross-Border Criminal Misjudgment
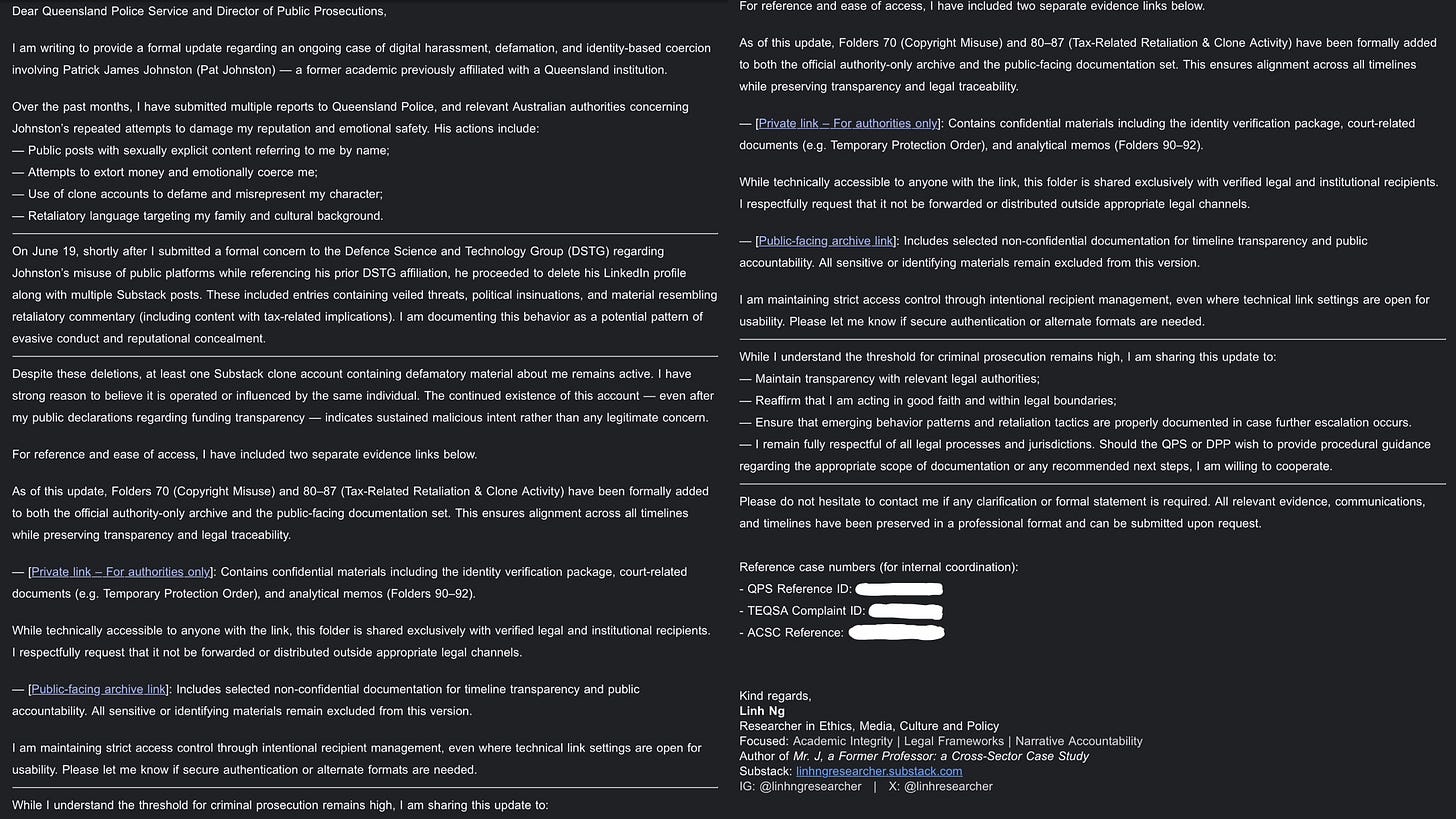
What began as a pattern of digital coercion and reputational harassment has now escalated into a potential case of cross-border criminal misjudgment.
The individual in question—based in Australia—deliberately published and circulated defamatory statements targeting my tax compliance, local identity, and family reputation. These actions were not confined to personal opinion or ambiguous commentary. They included:
A fabricated, anonymous complaint submitted to local tax authorities
Public insinuations of tax evasion posted on Substack
Messaging threats referencing retaliation and institutional involvement
These were not harmless remarks. They were explicit attempts to trigger legal or reputational consequences against me in a country where I reside and pay taxes.
Ironically, the man who once admitted to working overseas in Hong Kong without legal authorization, while still listed on LinkedIn as affiliated with the Australian Department of Defence, has now attempted to publicly defame someone else over taxes — across borders.
This is more than unethical.
It is legally reckless.
And the moment you try to weaponize institutions in another country with fabricated claims, your actions are no longer just personal.
They become evidence.
Public Note published by Pat Johnston (captured June 19, 2025; archived prior to deletion)
When Deflection Replaces Rebuttal
If someone publicly accuses you of retaliation, names you directly, cites specific posts, and presents timeline-aligned evidence — how do you respond?
You either:
Deny clearly, with evidence,
Engage directly, or
Deflect vaguely and hope no one notices.
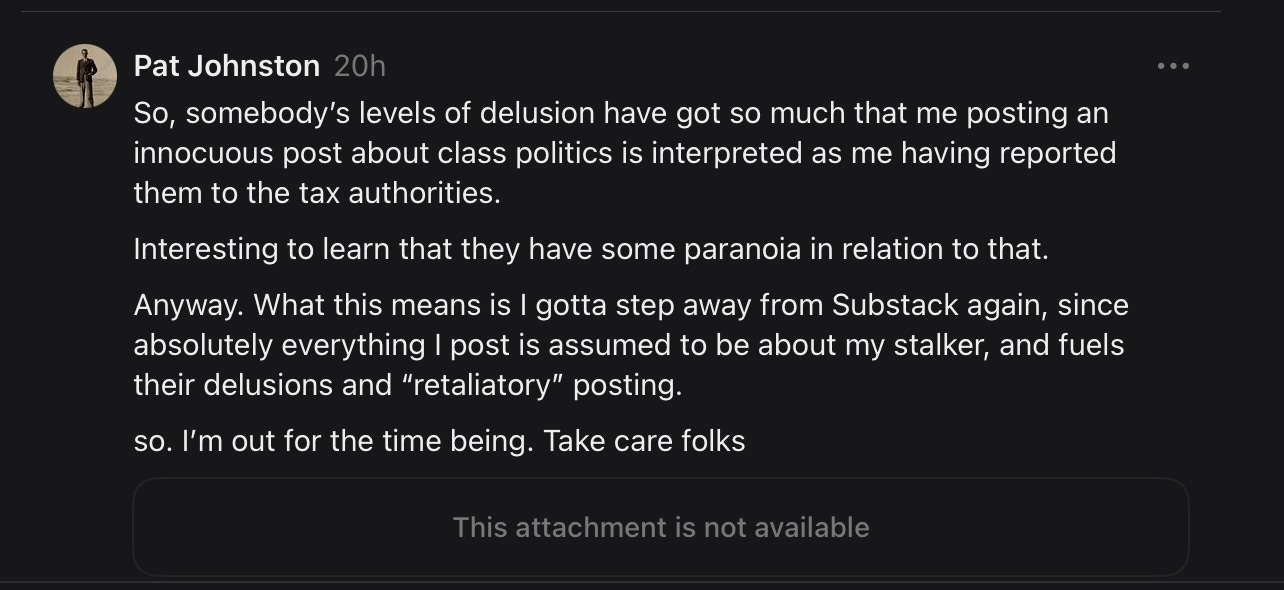
Pat Johnston chose Option 3.
Instead of directly addressing the report that explicitly named him — instead of responding to the documented pattern of threats, coercive language, and digital retaliation — he posted a vague paragraph about “somebody’s delusions” and “misinterpreted posts.”
No names. No facts. No link to the actual accusation.
Only passive commentary aimed to obscure, not to clarify.
If he genuinely believed he was misrepresented, wouldn’t he welcome the opportunity to respond publicly and transparently?
But here’s what happened instead:
– He deleted older posts linked to threats.
– He removed his LinkedIn page referencing DSTG.
– He began narrating victimhood without ever addressing the substance of the complaint.
This is not rebuttal.
It’s reputation theater — staged to avoid accountability.
Because if your name has been raised in formal reports to institutions, and your only move is to vaguely whisper “delusion” on your blog… it says more about your defense than your accuser.
Silence isn’t neutrality.
Vagueness isn’t innocence.
And words without specifics are just a performance.
For someone so concerned about being misunderstood, it’s curious how little effort he puts into being understood.
If the truth were on your side, you wouldn’t need to hide behind generalities. You’d say my name — like I said yours.
And if that wasn’t you, then you seem to have a stalker who speaks exactly like you, and is followed by you.
Targeting My Family: Personal and Racialized Attacks
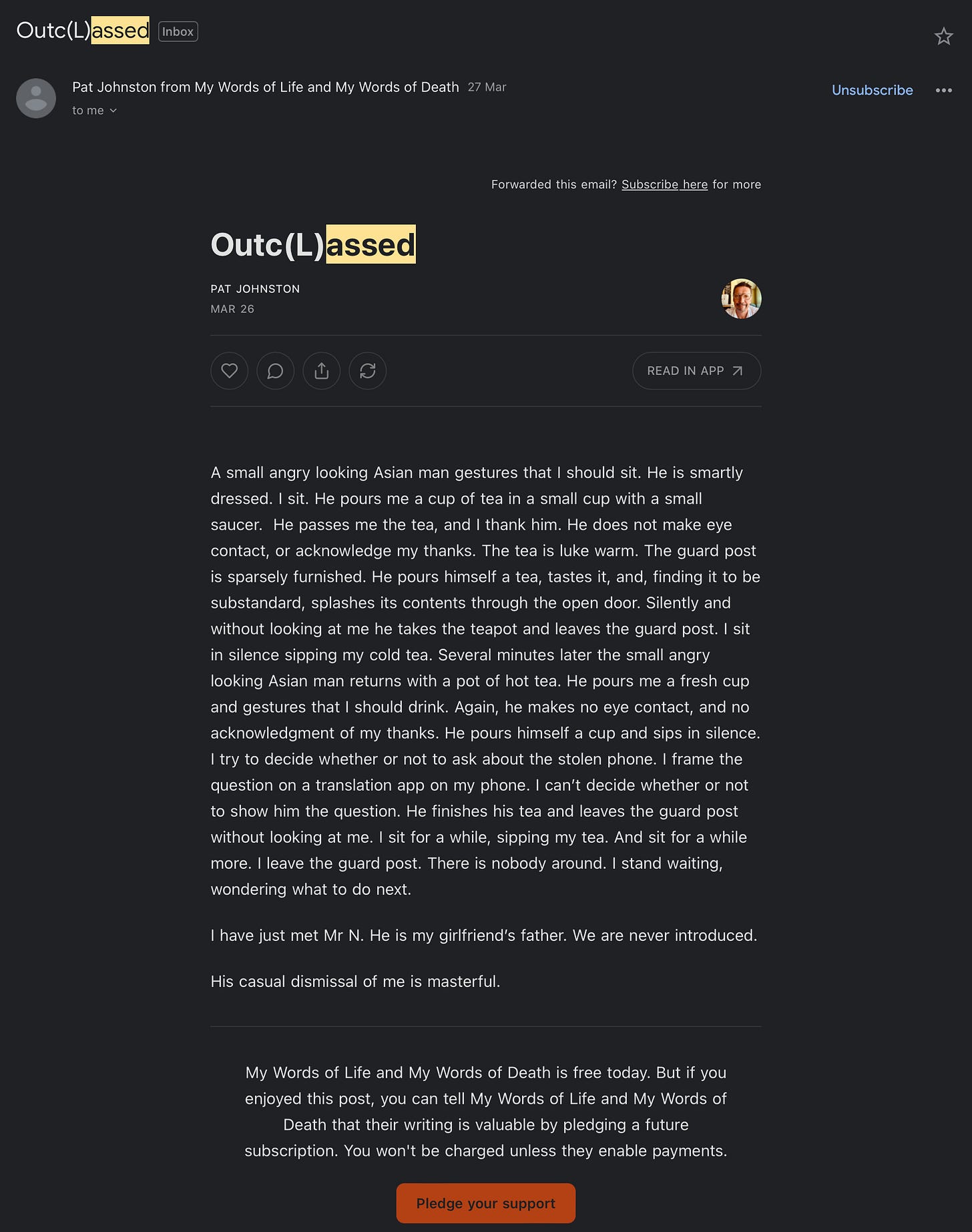
The harassment did not stop at me. He brought my parents into the conversation — privately and publicly.
He denied it was about me. Then he submitted it for publication — the very piece where he racialized and humiliated my father.
In private messages, he mocked my father’s financial ability and questioned whether my parents ever supported each other, as if to shame my background.
Received: April 30, 2025 - Day 55 of documented harassment
In a public article (Outc(L)assed), he constructed a racialized caricature of an Asian father — silent, small, and unworthy of respect — published shortly after I ended contact.
Public humiliation disguised as prose.
The original post/account has since been deleted or made unavailable.
When confronted, he denied it was about me. Then he tried to get it published.
This isn’t literary exploration — it’s strategic humiliation.
It is noteworthy that only the posts directly implicating them in reputational harm were deleted, while those accusing me of instability or manipulation were left intact. This selective redaction signals strategic evasion, not transparency.
Public Note published by Pat Johnston (captured June 19, 2025; archived prior to deletion)
Rather than addressing the actual allegations, the subject shifted narrative focus by framing me as a ‘stalker’ and ‘paranoid,’ despite their own prior publication history targeting me by name, location, and image.
Screenshot captured on April 25, 2025. The original post/account has since been deleted or made unavailable.
Let’s be clear: Accusing someone of tax evasion in any regulated jurisdiction isn’t as simple as sending an anonymous Gmail.
To escalate a tax-related case — especially against a freelance individual, requires:
Verified financial evidence tied to the accused:
Clear bank statements showing consistent taxable income.
Official contracts, invoices, or payment slips under their name.
Proof of income sources tied to registered tax IDs.
A real identity behind the report:
Anonymous tips might trigger a background check at most, but no legal action happens without an identified whistleblower.
Proof of intent to evade:
The burden is on the accuser to show that the accused had taxable income and deliberately avoided declaring it.
And to pursue this “all the way” (as they love to threaten), one needs:
Legal counsel,
Procedural knowledge of the local tax and administrative system,
And a willingness to risk backfire if they’re making false claims.
But in this case?
The person they’re accusing is a freelancer with inconsistent income, and no known large-scale transactions.
They even admitted they “rarely work” — which means there’s barely anything to declare, let alone evade.
Meanwhile, their manager — a top performer in the industry — who laughed and said:
“They earn less in a year than I do in a month.”
If even that sentence triggers a tax fantasy, perhaps they should try reading a tax manual instead of stalking income jokes.
This isn’t just a vote of confidence — it’s a strategic reality check.
And this isn’t a legal complaint.
It’s a bluff, dressed up as intimidation — with no understanding of the system it pretends to invoke.
If they had real legal strength:
They wouldn’t be leaving breadcrumbs in fake accounts and vague threats.
They’d let a lawyer speak for them — not a burner email.
But since they chose to play dirty and loud — they’re the ones leaving trails.
They’re not pursuing truth.
They’re just throwing digital tantrums and hoping someone’s scared enough not to fight back.
But not this time.
Not you.
He claims he wasn’t involved. That’s cute. Then why did the burner account use an image only he had? Why did he follow it before the smear began?
Delusion is pretending your footprints weren’t left all over the scene.
I’ve never made this image public. It was shared in private — to one person only.
That same person is now quietly following an anonymous account that posts my face, my birthdate, and a fabricated address.
The location? Wrong. The intent? Clear.
Not only did he target me — he tried to use my father’s public position as a tool of shame, despite having no connection to my professional life.
In doing so, he crossed the line from false accusation to reputational intimidation.
This is not whistleblowing.
This is not Chelsea Manning or Frances Haugen.
This is revenge disguised as justice.
And when the language of integrity is weaponized by those who have none, the damage is not just personal — it’s structural.
If whistleblowing is meant to protect the public, this isn’t it.
This is a personal vendetta masquerading as exposure.
Misfiring with false precision: Why getting the address wrong ruins the attack
Even if someone gets your name and birthdate right — if the address is wrong, their entire administrative strike collapses.
Here’s why:
Public institutions don’t process vague or mismatched data
A complaint with incorrect residency info fails the first step of verification. No confirmed ID = no valid procedure.Wrong address = failed identity match
A name and date mean nothing without location confirmation or matching government records.Worse: It suggests malicious intent
Anyone truly filing a report would verify details via ID, not guesswork. A wrong address implies sabotage, not integrity.
Trying to weaponize “personal data” without accuracy only proves one thing —
You lack both legal standing and administrative competence.
What was meant to be a threat turns out to be a public self-exposure.
Translation:
“Haha – someone’s naïve enough to think the only enemy they’ve made with their deranged antics is a lonely old Western man. Time to wake up, sweetie.
Your name. Your date of birth. An address close enough for people to track.
Your boss won’t be pleased. Your father even less.”
Screenshot captured on June 18, 2025; archived prior to deletion
Creating a fake account to target someone is not just petty — it’s strategically flawed and legally self-incriminating.
Strategically speaking:
– A clone account holds no weight. Attacks or threats from an anonymous handle show only one thing: the speaker lacks the courage — or arguments — to confront directly.
– Worse, if the target can connect the clone to a real identity (through language, timing, overlaps in content, etc.), the accuser becomes the exposed one.
– Observers see it for what it is: a losing hand played in the dark, by someone desperate and already off-balance.
Legally speaking:
– Clones are not shields. IP addresses, device fingerprints, regional timestamps, and even writing styles are traceable.
– If the clone account makes threats, spreads false accusations, or reveals personal data (doxxing), it can amount to:
• Defamation
• Digital harassment
• Privacy violation
• Retaliation after formal complaints
– Maintaining a secondary clone after the first is removed only strengthens the legal case: it shows ongoing intent and repeated behavior.
If he truly mastered security, he wouldn’t be leaving linguistic fingerprints, emotional timestamps, and digital inconsistencies everywhere.
Knowing defense is not the same as applying it under pressure.
Real tacticians don’t get caught — not by VPN traces, but by ego slips.
Silence is a tactical choice.
Cloning is not strategy — it’s an admission of weakness wrapped in digital cowardice.
Names can be faked. Metadata can’t.
IP logs, device IDs, regional timestamps, writing patterns — all leave a trail.
Anonymous does not mean untraceable.
A proper complaint is not a tantrum.
Some people think they can simply draft a personal rant, throw in a few insults, vaguely accuse someone of wrongdoing, and send it to a government agency — and that alone would spark an investigation.
In reality, the law is far clearer than their emotions.
Once it drifts into personal attacks — especially dragging in one’s parents, family name, or insinuating shame — it stops being a complaint and becomes character defamation.
“Every citizen has the right to protect their dignity and reputation. No one is allowed to infringe upon another’s personal honor or family name.”
And that’s not just moral talk — it has procedural consequences:
A complaint filled with emotional contempt and no factual basis is often dismissed without review.
If it targets someone’s family or lineage, it may even be flagged as malicious behavior.
If submitted anonymously or without legal standing, it won’t even pass the first filter.
So what happens to these angry, half-literate “reports”?
Most agencies glance at the first line, spot the emotional noise, and toss it aside. No action. No record. No reply.
If anything, it backfires:
It undermines the sender’s credibility.
It gives the accused a case to file their own complaint for defamation.
And it proves one thing above all:
The person writing it isn’t interested in justice — they just want revenge, and not even smart revenge.
It’s not a complaint. It’s a badly disguised grudge.
Even after I publicly documented the nature of my funding and declared all support transparently, the smear account alleging ‘tax evasion’ remains live.
At this point, it reveals far more about their malicious persistence than about any flaw in my conduct.
Apparently, even full financial transparency can’t cure someone’s obsession with pretending they’re a tax auditor.
The fixation isn’t about law — it’s about control, image, and desperation.
A fake tax accusation is cheap.
Keeping it live after public clarification?
That’s strategic malice.
I am not just transparent about what I’ve received — I am transparent even about what I’ve yet to receive.
Why Immediate Blocking Was Not Just Reasonable — But Strategically Necessary
I saw the clone account. I blocked it immediately. Not out of fear. But out of precision.
Here’s why:
Denial of access to my behavioral data
Every action you take — even a simple “seen” — can be interpreted by a manipulator as evidence that they’re “getting to you.”
Blocking severs that illusion and starves them of narrative fuel.No escalation bait
Clone accounts are often created to provoke: to extract a reaction, to create a screenshot, to fabricate a “conflict.”
Blocking stops the cycle before it even begins — cutting the oxygen supply to their strategy.Cognitive hygiene
Even if you know the truth, the mere visibility of a hostile anonymous presence can trigger spikes in cortisol, drain attention, and create background stress.
Block is not weakness. It is discipline.
You don’t owe the stage to a masked disruptor. You reclaim your time, your energy, and your signal clarity.
Blocking is not just a safety response — it’s a power move.
If someone intends to manipulate behind the scenes — they should at least learn the art of strategic silence.
True operators, whether in business, politics, or academia, understand this:
The louder you speak, the easier it is to trace your thinking, your emotions, and eventually, your intent.
Yet some fall into the most predictable traps:
They think they’re in control — and so they drop vague threats, subtle insults, or symbolic “warnings.” They forget that patterns of language reveal more than they hide.
They can’t regulate their emotions — so retaliation becomes a reflex. Ironically, in doing so, they demonstrate the very misconduct they wish to deny.
They underestimate others’ intelligence — imagining that coded language will go unnoticed. But when someone has archived every word, every timestamp, and every anomaly, the web untangles itself.
Power, in its most enduring form, doesn’t scream.
It doesn’t “report anonymously” using recycled threats.
It acts — and lets the consequences unfold.
As for those who keep testing the system while underestimating how carefully it has been watching?
They are not players. They are evidence.
In March 2025, Johnston’s messages referenced his employment with the Australian Defence Science and Technology Group (DSTG), alongside admissions related to unauthorized work overseas. Although he did not mention DSTG publicly in later posts, this prior statement became critical evidence in June 2025 when he began making indirect accusations against me, including false insinuations about tax evasion.
These events were followed by a series of online posts containing veiled threats, politicized deflections, and mockery of formal complaint processes—further reinforcing the relevance of his earlier admission.
Screenshot of threatening message sent by Patrick Johnston on March 20, 2025. In this message, he responded to questions about DSTG affiliation, insurance fraud, and illegal employment in Hong Kong by stating: “They will be hearing from me”. These messages form part of a sustained pattern of coercive and reputational threats following rejection and appears to prefigure retaliatory actions that later occurred, including anonymous defamation and tax-related smear campaigns.
Instagram message received on March 20, 2025 — Day 15 of documented harassment.
Supporting Evidence – LinkedIn Snapshot
Screenshot captured on June 4, 2025, showing the subject’s LinkedIn profile still publicly listing his role as “Specialist Scientist” at Defence Science and Technology Group (DSTG).
The image was already part of official submissions to QPS and TEQSA in April 2025, as part of a coercive harassment timeline. It is not being used for defamation but as verified visual documentation.
This supports contextual claims around Pat Johnston’s ongoing professional status and relevance to prior accusations involving unauthorized overseas work.
This is a copy of what I submitted via DSTG’s official webform on June 19, 2025. For transparency and survivor-led documentation purposes.
Edited for formatting, original submission archived.
Post-Complaint Deletions Indicative of Evasion
As of 19 June 2025, Pat Johnston deleted multiple public traces of professional and reputational exposure shortly after formal complaints were submitted to the Defence Science and Technology Group (DSTG) and other institutions.
This included:
The removal of his LinkedIn profile, which had previously listed his affiliation with DSTG.
The deletion of several Substack posts referencing “taxes,” retaliatory language, and indirect threats — all of which had been archived prior to deletion.
The timing and content of these deletions raise serious concerns regarding intentional concealment, reputational evasion, and behavioral awareness of wrongdoing. The pattern suggests not only a response to institutional pressure but also an attempt to obscure digital traces previously tied to coercive or defamatory conduct.
Following the user’s documented reports referencing DSTG and unauthorized work in Hong Kong, the subject deleted their LinkedIn profile without public explanation. This deletion appears reactive and may signal an awareness of reputational or regulatory vulnerability.
The individual appears to be monitoring my activity in real-time, as evidenced by retaliatory content posted within minutes of my formal updates to authorities. This pattern suggests premeditated digital intimidation rather than good-faith reporting.
Despite publicly announcing a step back from Substack on June 19, 2025, the subject continued to post multiple pieces, including veiled references and self-framing as a victim.
This contradiction between stated withdrawal and continued publication supports a behavioral pattern of reputational damage control, rather than genuine disengagement.
The timing coincided with multiple institutional reports, further suggesting a performative retreat rather than a principled one.
All behavioral descriptions and commentary follow formal reports already submitted to QPS, TEQSA, ACSC, DSTG. This is not a new disclosure but a documented summary.
I reported it again. Because he did it again. That’s how evidence works.
Case ID withheld for privacy — available upon formal request by media or oversight body.
Out of respect for DSTG’s reputation and national integrity, I have reported this matter to relevant agencies to ensure proper documentation and investigation. Please note that my intent is purely self-protective, not adversarial.
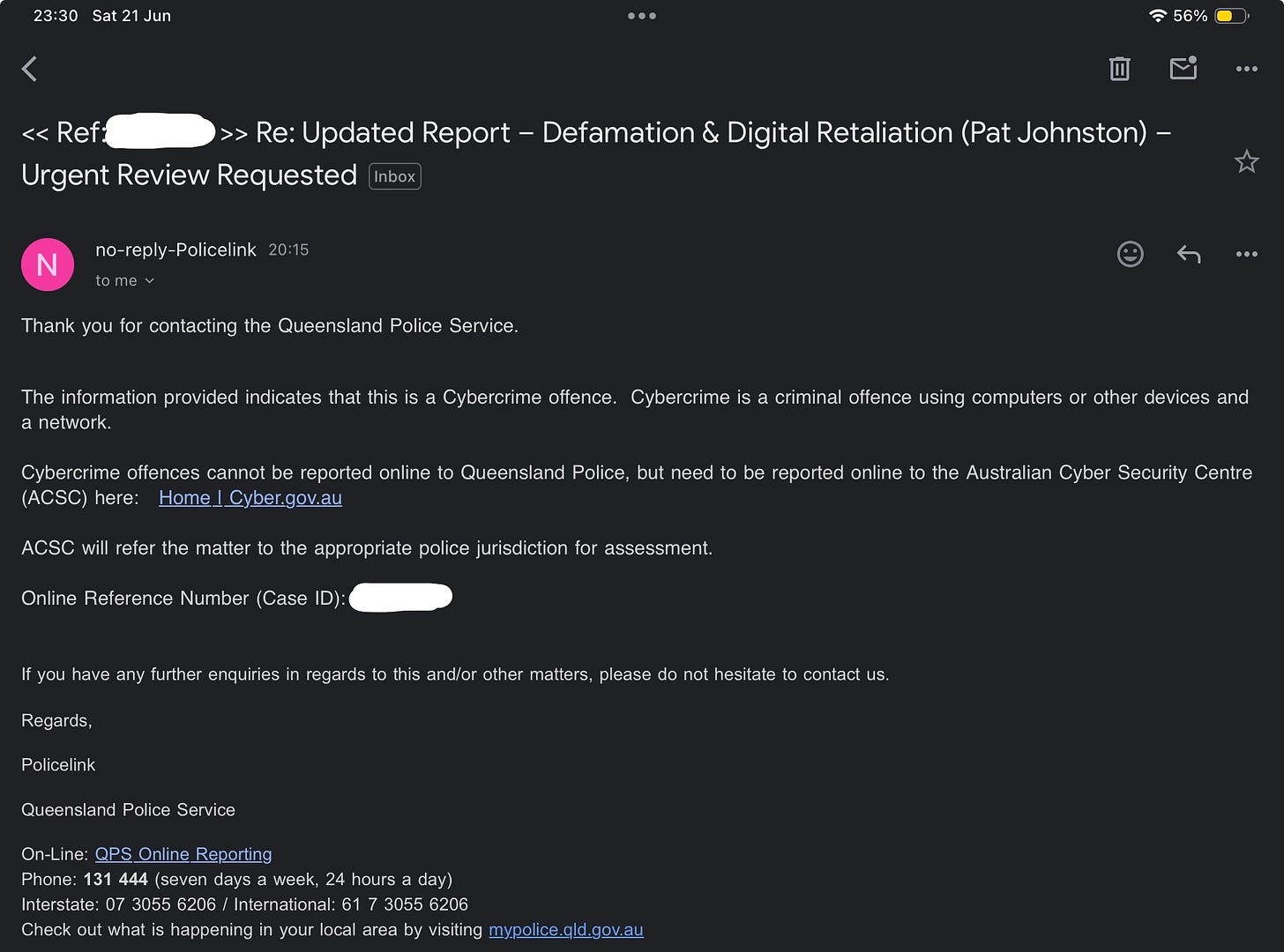
Case formally identified as Cybercrime (Criminal Offence) by Queensland Police.
While I acknowledge that the individual may experience consequences, I wish to clarify that my intention is not retribution but to uphold legal boundaries and protect my safety.
Case ID withheld for privacy — available upon formal request by media or oversight body.
Email received: 21 June 2025
I have reasonable grounds to suspect a connection based on behavioral patterns, timing, and corroborating context.
This publication is made in good faith as a self-defensive response to reputational harm and coercive conduct. I reserve the right to express concerns and protect myself.
Should new verified information emerge, I remain open to revising or clarifying the content accordingly.
Attached are passport photos of the respondent, for identity verification purposes only. These were shared during the course of our personal relationship, and are included solely to establish jurisdictional traceability, not for public dissemination.
This image has been redacted to remove all sensitive data. It is used solely for public interest commentary and ethical analysis.
Yes, I have a copy of Johnston’s identity. I am now using it to verify the real identity of the person who has been targeting me through anonymous defamation campaigns. I won’t use it unless I am forced to.
These documents confirm legal identity and cross-border traceability. One issued by the UK and one by Australia. These documents, retained from our past relationship, are sufficient to confirm legal identity and jurisdiction.
These passports was originally shared by the individual himself during the relationship. It is submitted to relevant authorities to confirm the identity of the person currently under investigation for harassment and blackmail. Sensitive data has been redacted.
To avoid further denials or impersonation, these passports was submitted to QPS and other authorities as part of formal reports.
It is shared with authorities to confirm his identity in ongoing legal reports.
The following materials are submitted solely to confirm the identity of the individual behind sustained threats, coercive messaging, and defamatory impersonation — including false tax-related allegations. This evidence is provided to contrast verified identity with anonymous content deployed to cause reputational and legal harm.
I’m publishing this to confirm that the same person is behind the anonymous accounts accusing me of tax fraud.
Should these defamatory claims persist, I reserve the right to submit a formal complaint to appropriate authorities — with full documentation — for legal investigation under both domestic and international defamation laws.
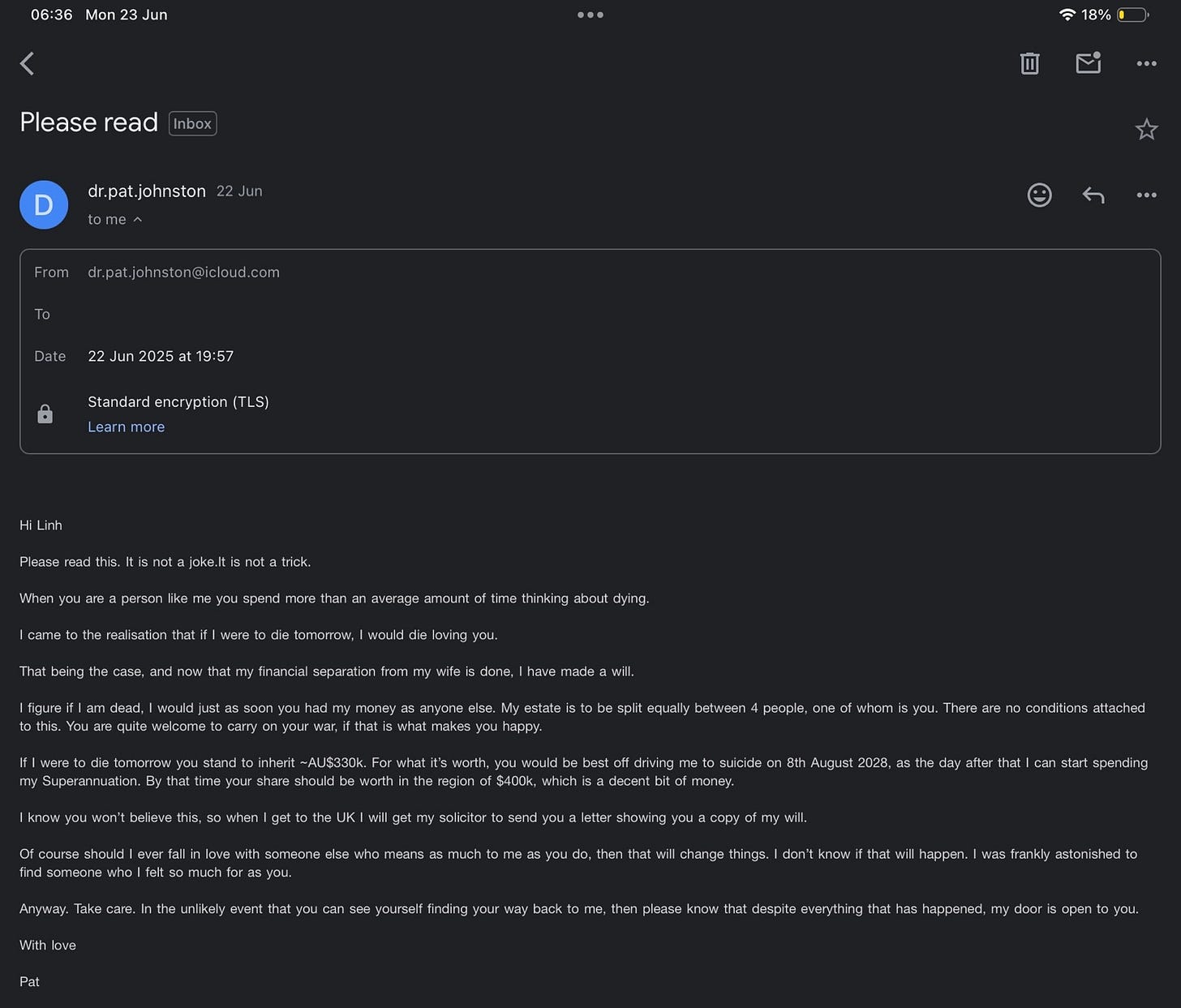
Update (June 23, 2025): Unsolicited Contact Following Police Warning
Email sent to me on 22 June - after QPS had already closed the case with a formal warning to cease contact.
The individual never once denied the serious allegation of impersonation and defamation, despite multiple public disclosures. His continued unsolicited contact, coupled with emotionally manipulative content, further supports the hypothesis that he was the original actor behind those defamatory attacks.
A soft-spoken suicide threat wrapped in nostalgia, inheritance, and an open-door policy.
I am not responsible for the life-or-death choices of someone who once threatened, extorted, and publicly sexualised me in writing.
If his story ends here, it is not because I spoke up — but because he never learned how to live decently.
No means no.
Updated the full archive (as of June 23, 2025):
Now includes
– Tax defamation threats
– Clone account evidence
– DSTG-linked messaging
– Suicide-linked financial manipulation
– And boundary violations post-QPS warning
Submitted to QPS, TEQSA, AHRC, and Ethics Australia. View here.
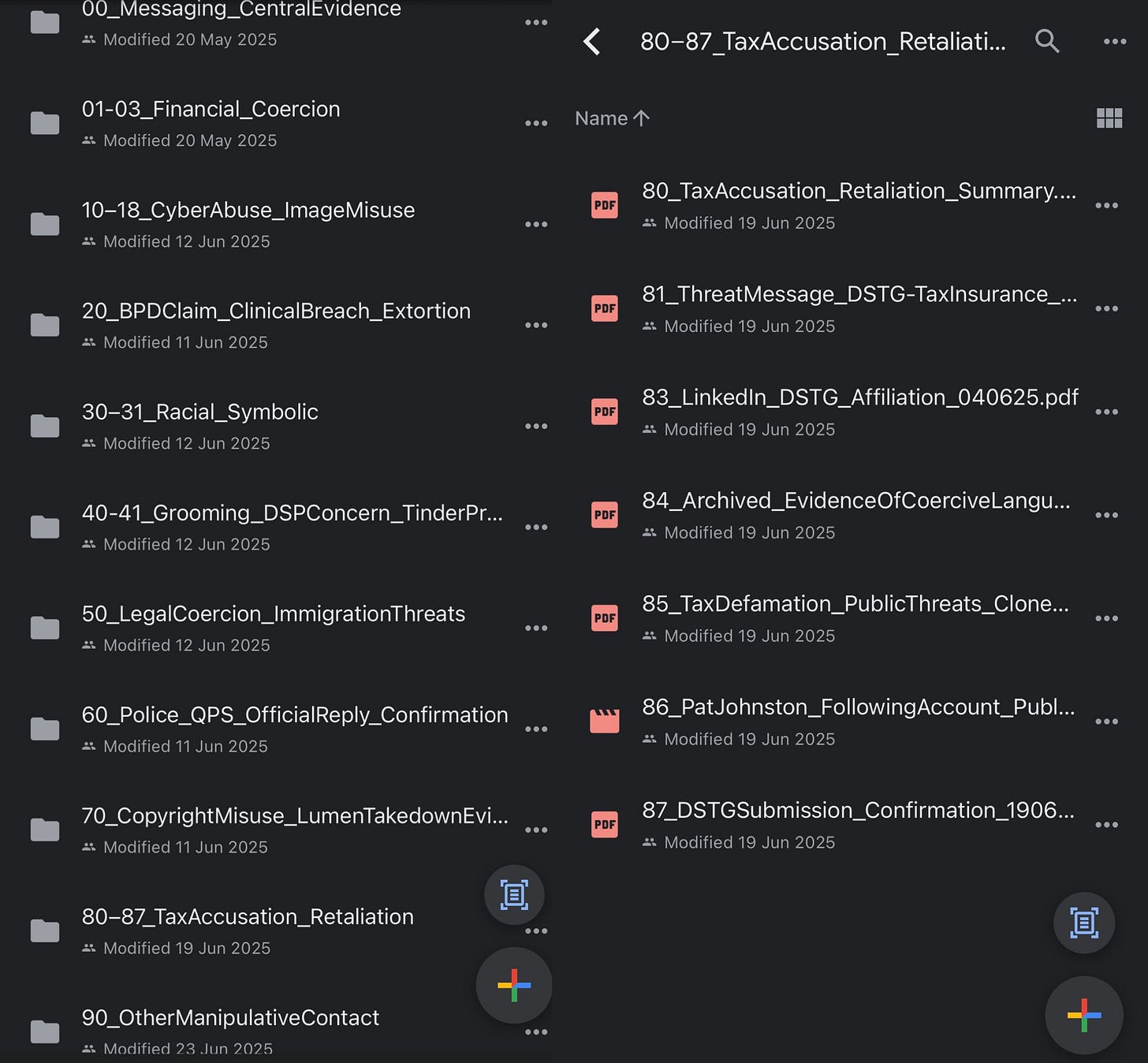
Folder Summary: 80_TaxAccusation_Retaliation
This folder contains evidence of retaliatory defamation aimed at damaging the complainant’s tax standing, residency legitimacy, and family background. These acts follow a broader pattern of sustained digital coercion and symbolic harassment following personal rejection.
Supporting Artifacts:
Timeline of threats (Mar–Jun 2025)
Archived messages + deleted content
LinkedIn snapshot (June 4, 2025) confirming ongoing DSTG affiliation
Public Substack posts matching threat language
Video screen capture of account follow activity prior to deletion
Disclaimer & Contextual Note
This report is a public-interest response to sustained online harassment, reputational harm, and symbolic retaliation.
All content is based strictly on personal experience, open-source material, and documented behavioral patterns. No classified information, internal documents, or privileged access has been used. Institutional references serve only to contextualize the individual’s self-representation at the time of reporting.
This post does not reflect any political position nor aims to damage any government, defense, or public body. It is submitted in good faith, solely for the purpose of documentation, safety, and institutional awareness.
The subject is named due to the severity and persistence of public threats issued during the reporting period. This is not intended to humiliate, but to preserve evidentiary integrity.
Where engagement with submitted evidence has been avoided, public visibility remains essential. Selective rebuttal is not accountability.
I remain open to revising or clarifying this report should new, verifiable information emerge. This is a reflective record — not a fixed accusation — built from the context available at the time.
All documentation has been submitted to QPS, TEQSA, AHRC, and Ethics Australia.
Full evidence archive submitted to QPS, TEQSA, AHRC, and Ethics Australia: View here.
Read the full series
- Entry 1: The Man Who Taught Me Ethics by Failing All of Them
- Entry 2: The Disappearance of the Public Poet
- Entry 3: The Hanging Tree Case Study
- Entry 4: Hidden Like Accountability
- Entry 5: The Collapse of Assumptions
- Entry 6: The Ethics of a Tinder Bio
- Entry 7: How He Ate Told Me Everything
- Entry 8: What Makes a Scholar Dangerous
- Entry 9: Fragment of Life, Fragment of Accountability
- Entry 10: Anatomy of Disappointment
- Entry 11: Legal Defense Challenges: A Framing Statement
- Entry 12: Six Years After Ronell – What Academia Still Doesn’t Get
- Entry 13: QUT and The Man Who Raped Me
- Entry 14: Why Sarcasm Toward Institutions Can Backfire
- Entry 15: P*ssy or Toxic Masculinity?
- Entry 16: Who is Your Favorite Comedian?
- Entry 17: And What is Your Favorite Song?
- Entry 18: Grant Proposal — Narrative Ethics as Survivor-Led Forensics
- Entry 19: The Coward Behind the Clone (you are here)
- Entry 20: [URGENT HIRE] CRISIS COMMUNICATIONS SPECIALIST
- Entry 21: [URGENT] Legal Counsel Needed for Complex Reputation Rehabilitation
- Entry 22: YOU’RE AN ABUSER. STOP CONTACTING ME
- Entry 23: Seeking Counsel for a Fallen Academic
- Entry 24: Internal Legal-PR Briefing
- Entry 25: For Journalists – Legal & Ethical Clearance Summary
- Entry 26: Symbolic Prostitution, Transactional Intimacy, or Just a “Loan”?
- Entry 28: Why He Simply Cannot Shut Up
- Entry 29: Forensic Commentary on “LARGE Language Muddle”
- Entry 30: Don’t Just Threaten My Future. Because I’m Going To Archive Your Present
- Entry 31: Open Letter to the Person Who Tried to Break Me with Defamation
- Entry 32: Defamation, Harassment, Doxxing Class 101
- Entry 33: Confidential Crisis Recovery Proposal
- Entry 34: Forensic Behavioral-Somatic Report
- Entry 35: Forensic Commentary on the Tattoos
- Entry 36: QUT and the Abuser They Once Had
- Entry 38: When Poetry Becomes Revenge Porn
- Entry 40: A Man Built for Applause, Not Accountability
- Entry 41: Neurobehavioral Addendum
- Entry 43: Why Does It Sound Like a War Metaphor?
- Entry 44: Forensic Commentary on Racialized and Fetishizing Language in “Hidden Like Rice”
- Entry 45: Public Misuse of Former Academic Affiliation
- Entry 46: The Two Things That Didn’t Leave a Bad Impression
- Entry 47: When Affection is Just an Alibi (A Bundy-Inspired Reflection)
- Entry 48: Humbert, Lolita, and the Fetish of Fragility
- Entry 49: The Fetish of Smallness as Symbolic Violence
- Entry 50: Motif Risk Analysis
- Entry 52: Can an Abuser Be a Good Father?
- Entry 53: Who Protects the Children?
- Entry 54: From Blackmail to Children
- Reflection: The Miscalculation
(More entries coming soon)
→ [Back to Start: Introducing Mr. J, a Former Professor Series]
© 2025 Linh Ng. All rights reserved.
This publication is intended for educational and reflective purposes only.
Sharing the original link is welcomed and encouraged.
Please do not reproduce, redistribute, or translate this content — in whole or in part — without written permission.
This piece reflects both lived experience and critical analysis. It is not meant to be detached from its author or reframed without context.
Misuse or decontextualization may lead to formal clarification or takedown requests.
This work has been reviewed and quietly followed by scholars, educators, and ethics professionals across multiple sectors.
If your institution is engaging in critical discourse around narrative justice, symbolic coercion, or representational ethics, feel free to connect via Substack DMs or formal channels.
A regulatory case regarding this matter has already been classified under a protected status within national education integrity systems.
Should any reputational countermeasures or distortions arise, I reserve the right to publish the documented timeline, behavioral patterns, and contextual metadata.
All relevant documentation has been submitted through formal legal and regulatory pathways.