Mr. J, a Former Professor Series – Entry 38: When Poetry Becomes Revenge Porn
How a Professor Sexualised My Body
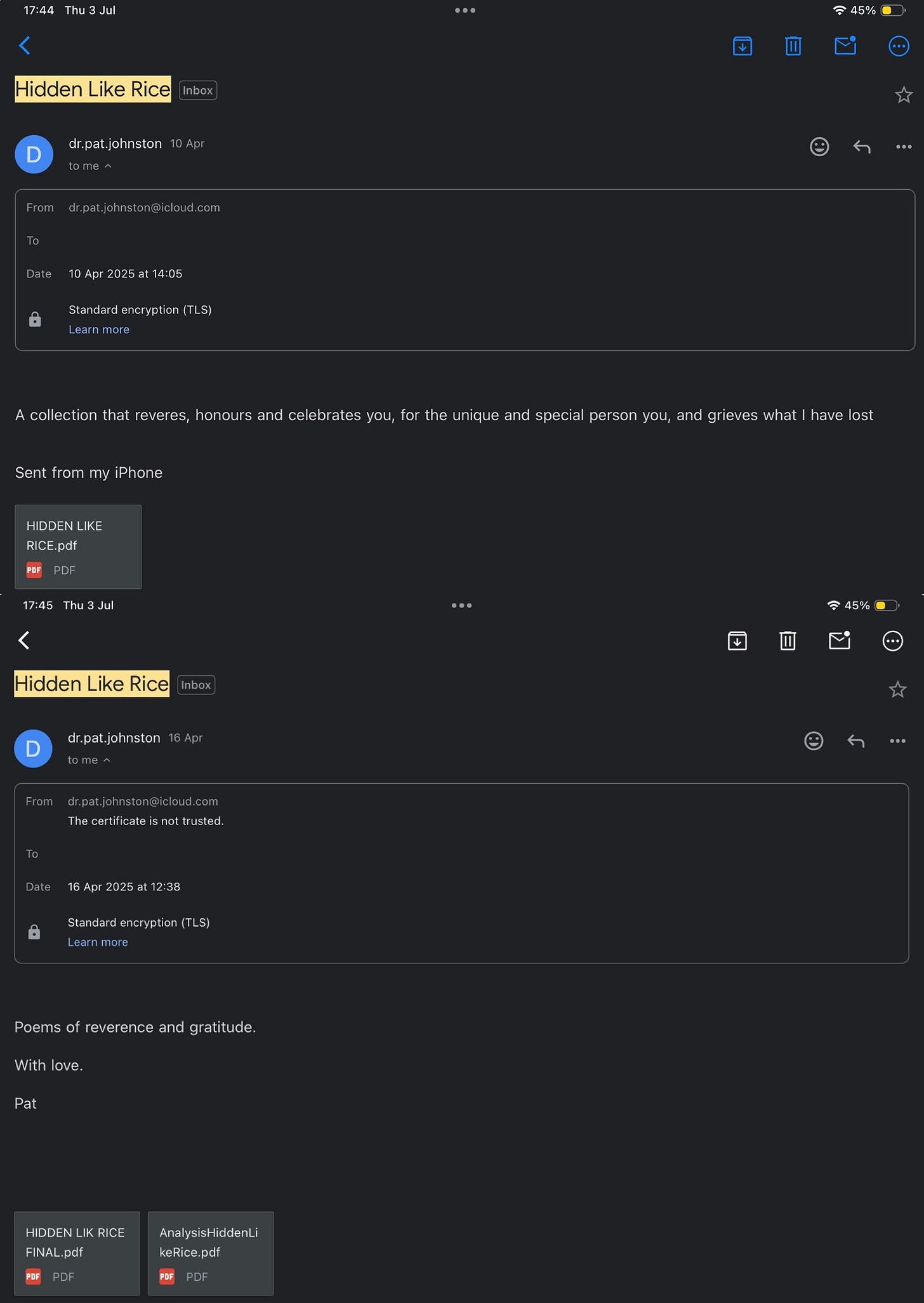
In April 2025, I received a message from a man who had once been my partner — a former professor who no longer taught, but still cloaked himself in the dignity of literature. It was a poem.
Emails received: April 16–30, 2025 (Days 36-42 of documented harassment)
Or so he called it.
The email came after multiple no-contact requests. It arrived uninvited, describing my body in graphic, hyper-personal detail:
“hot cunt”
“tiny breasts”
“slit navel”
“pheromone haze”
There were no images. No videos. Just words. But these words functioned like a scalpel: slicing into memory, rewriting boundaries, and reasserting control — all under the poetic guise of grief and longing.
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
The Aesthetics of Coercion: Heidegger, Derrida, and Misused Theory
Some have described the poem as “literary.” In fact, it borrows heavily from philosophical language — cloaking abuse in poetics.
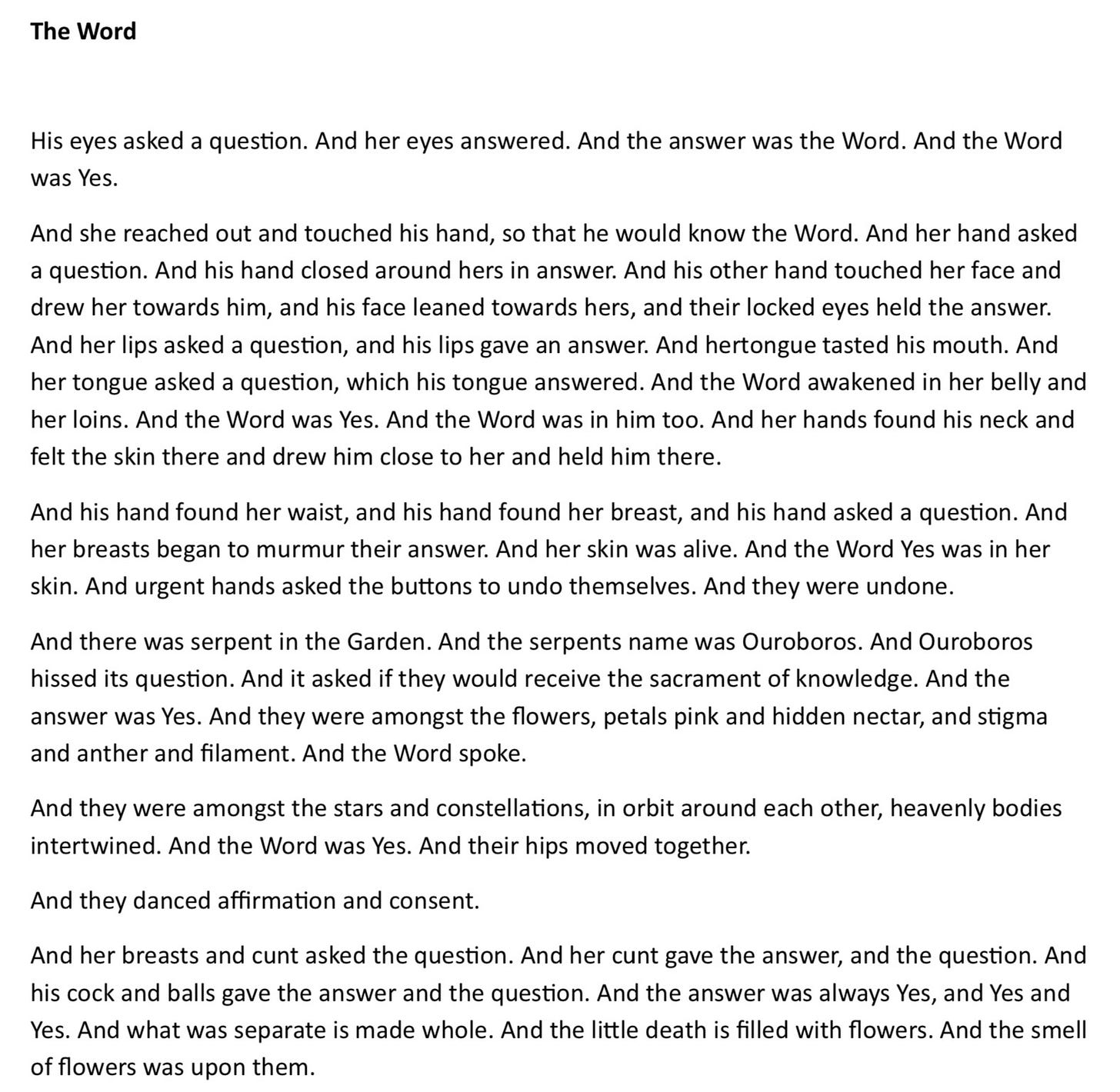
“There is no past. No future. Only this room.”
“Ouroboros. Eden. Sacrament.”
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
This “eternal present” aesthetic isn’t just about mysticism or existential beauty. It erases accountability by suspending time — suggesting that if nothing is fixed, nothing can be blamed.
But the most disturbing part lies in the way the poem speaks of consent:
“Her cunt gave the answer. And the answer was always Yes.”
It isn’t a metaphor of intimacy. It’s a textualized act of coercion. By attributing a “yes” to my body — without my voice — he effectively transformed my physical being into his mouthpiece.
It isn’t a metaphor of intimacy. It’s a textualized act of coercion. By attributing a “yes” to my body — without my voice. This is Derridean hospitality turned violent: the guest (my body) becomes a host to his desire, without consent, without choice.
My body cannot be your mouthpiece.
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
The Ronell–Reitman Parallel: Academic Poetics as Possession
This style mirrors the infamous Ronell–Reitman case, where authority cloaked itself in affectionate theoretical language to blur boundaries and claim ownership.
In this “poem,” he layered religious symbols (Ouroboros, Eden, sacrament) and references to Camus to suggest transcendence, as if violating boundaries could be rebranded as intellectual transcendence. The result? A gaslighting narrative that casts me as the seductress and him as the tragic, misunderstood scholar.
This wasn’t vulnerability. It was a strategy: pathos weaponized into obligation, grief twisted into leverage.
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
When Poetry Becomes a Trap
“You were half asleep / your hand in my pants / I’m sleeping… I’m awake. You laughed.”
This line mimics dream logic — unclear, poetic, allegedly romantic. But it’s not romantic. It’s narrative gaslighting.
This is the dangerous thing about literary grooming: it rewrites events as if the woman led them, and the man — middle-aged, grieving, intellectual — is just a vessel of feeling. It turns abuse into tragedy, coercion into art.
But art without consent is not art. It’s manipulation.
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
“You Asked Me Not to Publish, So I Wrote a Sex Poem and Sent It to You”
That’s the real title this poem deserves.
He called it a “poem of grief.”
No. It’s revenge porn for me — in literary disguise.
This was not just a poem. It was a symbolic violation — a form of literary exposure so intrusive it felt like being undressed without warning, watched without consent, and rewritten against your will.
If deepfake strips the image, this strips the memory. If one is digital rape, then this is poetic rape.
It was a final act of narrative control — to trap me inside his archive.
He didn’t need a camera. His pen was enough.
This wasn’t hospitality.
It was literary intrusion — offered as a poem, but crafted as possession.
The Aftermath: “Art” as Territorial Marking
He first published it publicly — a deliberate display to claim narrative ownership over my body and memory. Only after being called out did he take it down, then attempt to reassert control by sending it privately, as if offering a personal “gift” of intimacy.
It was never about healing or expression; it was always about reminding me who held the pen.
When someone weaponizes aesthetics to assert dominance, humiliation masquerades as tribute, and boundary-breaking is reframed as romantic devotion.
Final Words
If you read this and still think “it’s just poetry,” ask yourself:
Whose body was it about?
Whose consent was ignored?
Whose pain was re-written into a tragic myth?
I’m not here to erase his story. I’m here to reclaim mine.
Because when poetry becomes a way to re-sexualize a woman who already said no, it is no longer a poem.
It becomes evidence.
Who Are Heidegger and Derrida? A Brief Context
Martin Heidegger (1889–1976) was a German philosopher influential in existential and phenomenological thought. His seminal work Being and Time (1927) explores human existence not as a static “what,” but as a dynamic “how” — shaped by memory, fear, hope, and temporal entanglement.
In the context of Pat’s poem, the line “There is no past / no future / only this room” reflects a pseudo-Heideggerian construction of an abstract, closed-off temporality — a “loop” designed to erase accountability and blur consent. When time becomes a sealed circle, the reader (and the woman written about) are trapped inside.
Jacques Derrida (1930–2004), a French philosopher, was the father of deconstruction and deeply interested in power dynamics embedded in language, especially around hospitality and consent.
In Of Hospitality, Derrida argues:
“When a guest is ‘welcomed’ into a home, they are always subordinate to the host. Hospitality always implies power.”
This suggests that what appears to be kindness or intimacy may actually conceal domination. If the guest cannot choose how to enter or leave, that hospitality is not truly free.
Update (June 10, 2025): Counter-Takedown Filed — Fair Use & Survivor-Led Documentation
On June 9, I received a formal DMCA notice from Google informing me that Patrick Johnston had submitted a copyright takedown request targeting my publicly accessible survivor evidence folders documentation already submitted to QPS as part of police evidence.
This content, previously submitted to law enforcement in the context of unwanted contact and coercive behavior, cannot retroactively be reframed as protected intellectual property for the purpose of silencing survivor documentation.
Any takedown request targeting such material constitutes a strategic misuse of copyright law, not a legitimate rights claim.
These files were published strictly under academic Fair Use and Fair Dealing protections, as part of an ethics-based documentation series. This takedown is not a valid copyright dispute, but a coercive response to institutional criticism.
Attempts to assert copyright over police-submitted evidence constitute a serious ethical and potentially legal breach. Such actions may be interpreted as obstruction of justice and retaliation against protected reporting
This is not copyright protection. This is reputational panic, disguised as a takedown notice.
The content was non-commercial, already submitted to Queensland Police (QPS) and regulators under official case IDs. Its removal constitutes an attempt to suppress documented harms rather than enforce legitimate rights. Misusing copyright mechanisms in this manner may qualify as a form of strategic litigation against public participation (SLAPP).
My publication falls squarely within the thresholds of:
Australian Copyright Act 1968 – Sections 41 & 42 (Fair Dealing)
U.S. Copyright Law – §107 (Fair Use)
International norms protecting public interest commentary and trauma documentation.
I have submitted a formal counter-notice. As per standard procedure, Google has forwarded the takedown request to the Lumen Database, where it is now publicly visible as part of platform transparency archives.
View takedown request on Lumen
If harassment persists, I reserve the right to escalate this matter to ethics boards, international legal monitors, and public interest watchdogs tracking strategic censorship and retaliatory misuse of institutional tools.
Any misuse of personal information obtained via counter-notice or takedown responses will be treated as further coercive harassment and may be reported to law enforcement under digital harm and privacy abuse frameworks.
No individual has the right to suppress survivor-led documentation solely on the basis of personal discomfort — especially when such material pertains to evidence already submitted to law enforcement.
Note on Naming:
The individual named in this piece is referenced due to the public nature and severity of their documented behavior, including threats and retaliatory writings.
The purpose of naming is not humiliation, but record integrity. When public responses fail to address the core evidence presented, transparency remains necessary.
Naming in this context reflects a duty to document — not to defame. Selective rebuttal does not equate to accountability.
Full evidence archive submitted to QPS, TEQSA, AHRC and Ethics Australia: View here.
Image Credit:
Photo Cover by Alexander Krivitskiy via Unsplash
Read the full series
- Entry 1: The Man Who Taught Me Ethics by Failing All of Them
- Entry 2: The Disappearance of the Public Poet
- Entry 3: The Hanging Tree Case Study
- Entry 4: Hidden Like Accountability
- Entry 5: The Collapse of Assumptions
- Entry 6: The Ethics of a Tinder Bio
- Entry 7: How He Ate Told Me Everything
- Entry 8: What Makes a Scholar Dangerous
- Entry 9: Fragment of Life, Fragment of Accountability
- Entry 10: Anatomy of Disappointment
- Entry 11: Legal Defense Challenges: A Framing Statement
- Entry 12: Six Years After Ronell – What Academia Still Doesn’t Get
- Entry 13: QUT and The Man Who Raped Me
- Entry 14: Why Sarcasm Toward Institutions Can Backfire
- Entry 15: P*ssy or Toxic Masculinity?
- Entry 16: Who is Your Favorite Comedian?
- Entry 17: And What is Your Favorite Song?
- Entry 18: Grant Proposal — Narrative Ethics as Survivor-Led Forensics
- Entry 19: The Coward Behind the Clone
- Entry 20: [URGENT HIRE] CRISIS COMMUNICATIONS SPECIALIST
- Entry 21: [URGENT] Legal Counsel Needed for Complex Reputation Rehabilitation
- Entry 22: YOU’RE AN ABUSER. STOP CONTACTING ME
- Entry 23: Seeking Counsel for a Fallen Academic
- Entry 24: Internal Legal-PR Briefing
- Entry 25: For Journalists – Legal & Ethical Clearance Summary
- Entry 26: Symbolic Prostitution, Transactional Intimacy, or Just a “Loan”?
- Entry 28: Why He Simply Cannot Shut Up
- Entry 29: Forensic Commentary on “LARGE Language Muddle”
- Entry 30: Don’t Just Threaten My Future. Because I’m Going To Archive Your Present
- Entry 31: Open Letter to the Person Who Tried to Break Me with Defamation
- Entry 32: Defamation, Harassment, Doxxing Class 101
- Entry 33: Confidential Crisis Recovery Proposal
- Entry 34: Forensic Behavioral-Somatic Report
- Entry 35: Forensic Commentary on the Tattoos
- Entry 36: QUT and the Abuser They Once Had
- Entry 38: When Poetry Becomes Revenge Porn (you are here)
- Entry 40: A Man Built for Applause, Not Accountability
- Entry 41: Neurobehavioral Addendum
- Entry 43: Why Does It Sound Like a War Metaphor?
- Entry 44: Forensic Commentary on Racialized and Fetishizing Language in “Hidden Like Rice”
- Entry 45: Public Misuse of Former Academic Affiliation
- Entry 46: The Two Things That Didn’t Leave a Bad Impression
- Entry 47: When Affection is Just an Alibi (A Bundy-Inspired Reflection)
- Reflection: The Miscalculation
(More entries coming soon)
→ [Back to Start: Introducing Mr. J, a Former Professor Series]
© 2025 Linh Ng. All rights reserved.
This publication is intended for educational and reflective purposes only.
Sharing the original link is welcomed and encouraged.
Please do not reproduce, redistribute, or translate this content — in whole or in part — without written permission.
This piece reflects both lived experience and critical analysis. It is not meant to be detached from its author or reframed without context.
Misuse or decontextualization may lead to formal clarification or takedown requests.
This work has been reviewed and quietly followed by scholars, educators, and ethics professionals across multiple sectors.
If your institution is engaging in critical discourse around narrative justice, symbolic coercion, or representational ethics, feel free to connect via Substack DMs or formal channels.
A regulatory case regarding this matter has already been classified under a protected status within national education integrity systems.
Should any reputational countermeasures or distortions arise, I reserve the right to publish the documented timeline, behavioral patterns, and contextual metadata.
All relevant documentation has been submitted through formal legal and regulatory pathways.