Mr. J, a Former Professor Series – Entry 48: Humbert, Lolita, and the Fetish of Fragility
Between Humbert and Johnston
Humbert Humbert, the unreliable narrator of Lolita, never truly loved Dolores Haze.
He did not see a girl — he saw a stage. A nymphet he could decorate, narrate, and imprison inside his carefully scripted fantasies.
His obsession was not with her humanity but with the illusion of control: the idea that he alone could define her story, her body, her worth.
Lolita (1962 film poster) (cropped). Published by Metro-Goldwyn-Mayer (MGM). Public domain. Source: Wikimedia Commons.
Projection, Not Affection
Humbert’s love was never about real intimacy. He was captivated by the reflection of his own desires: youth, power, and the intoxicating sense of ownership over something “untouchable.”
Similarly, in the emails I received — layered with poetry and nostalgic grief — he never saw me.
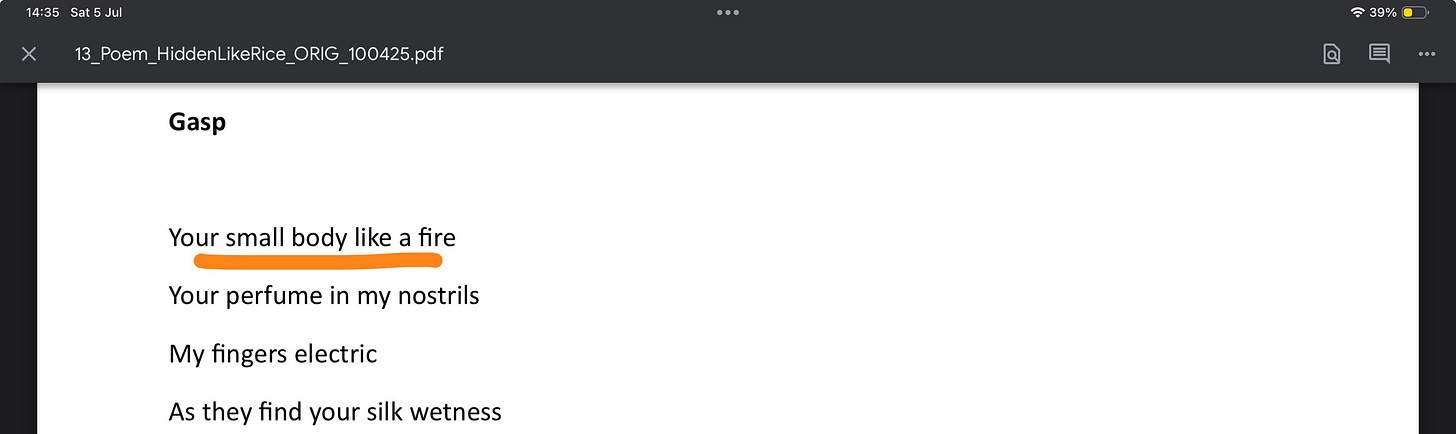
He saw a “tiny frame,” “hidden like rice,” “your small body like a fire.” He saw a symbol he could shape, not a person he could hold.
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
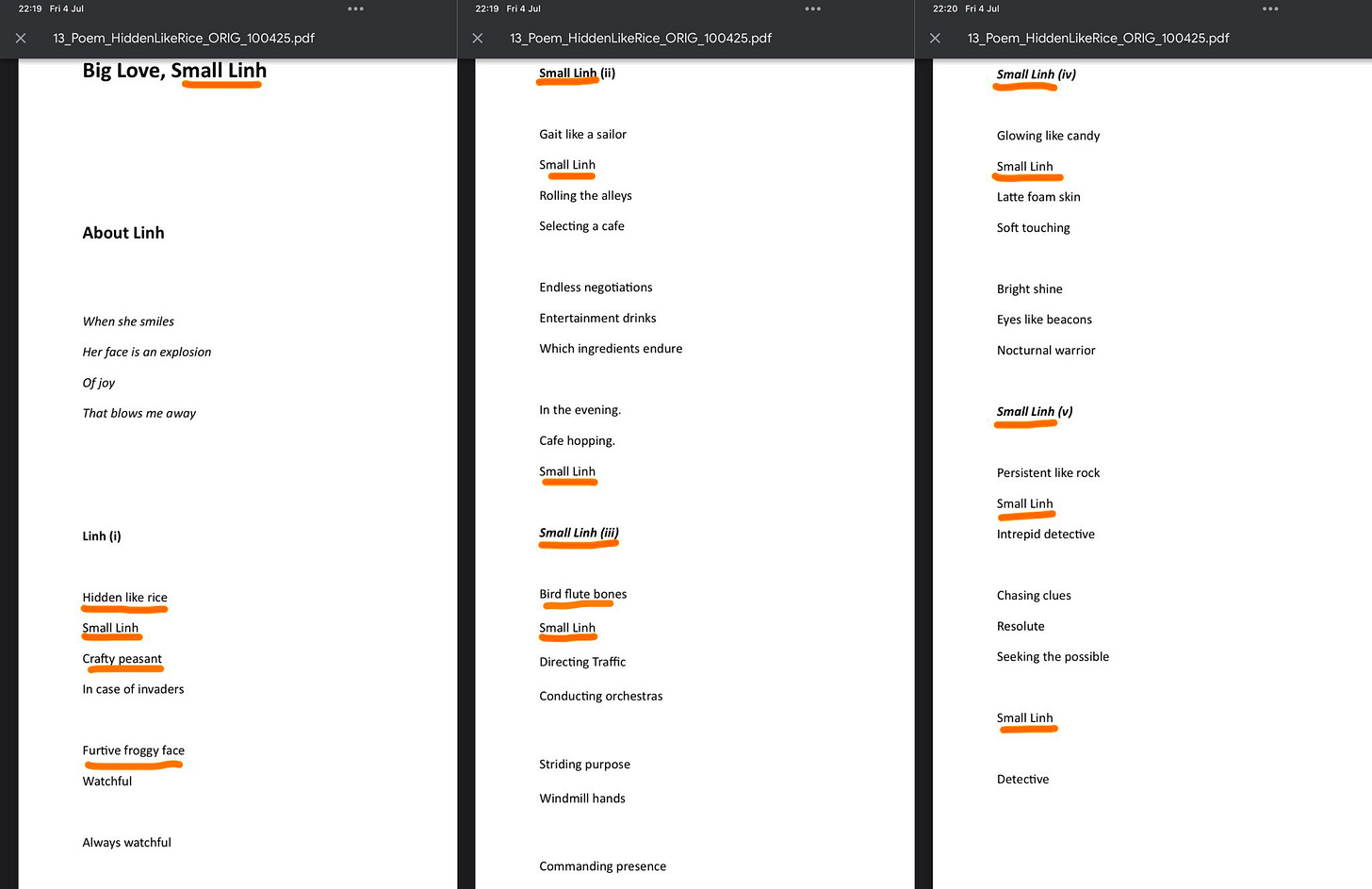
The Fetish of Smallness
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
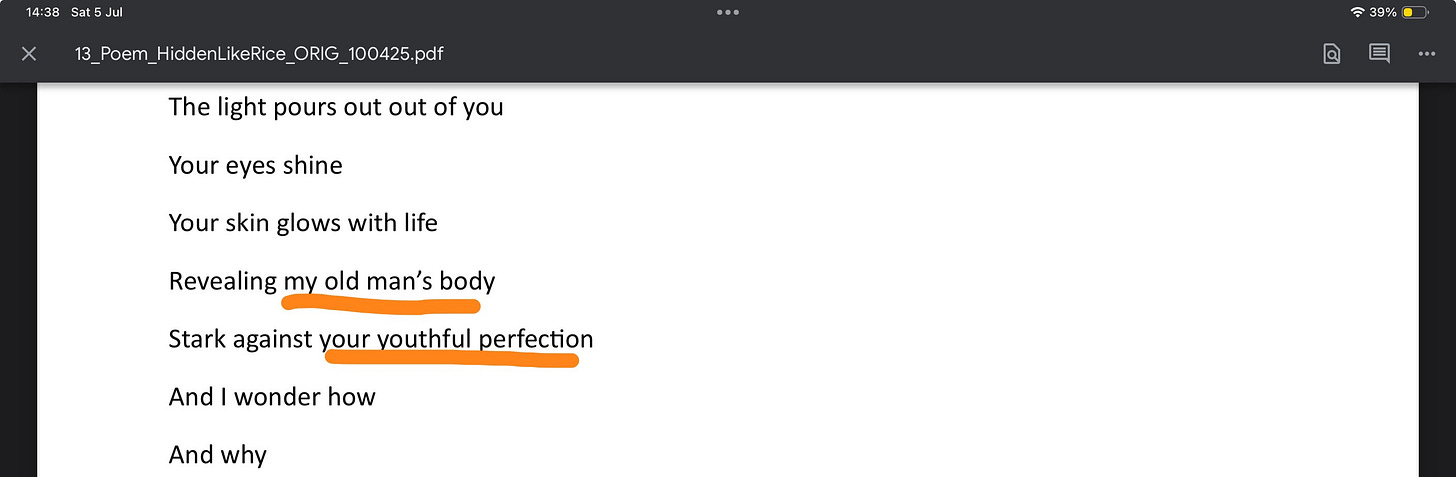
The repeated focus on “smallness,” “fragility,” and “delicate body parts” is no accident.
This is a classic fetish of control disguised as adoration.
By reducing someone to a fragile object — a tiny frame, a bird-like bone — the writer retains narrative supremacy. It is not an invitation to love; it is a move to dominate.
The False Promise of “Yes”
Written without consent. Screenshot retained for documentation purposes. Originally authored by Pat Johnston.
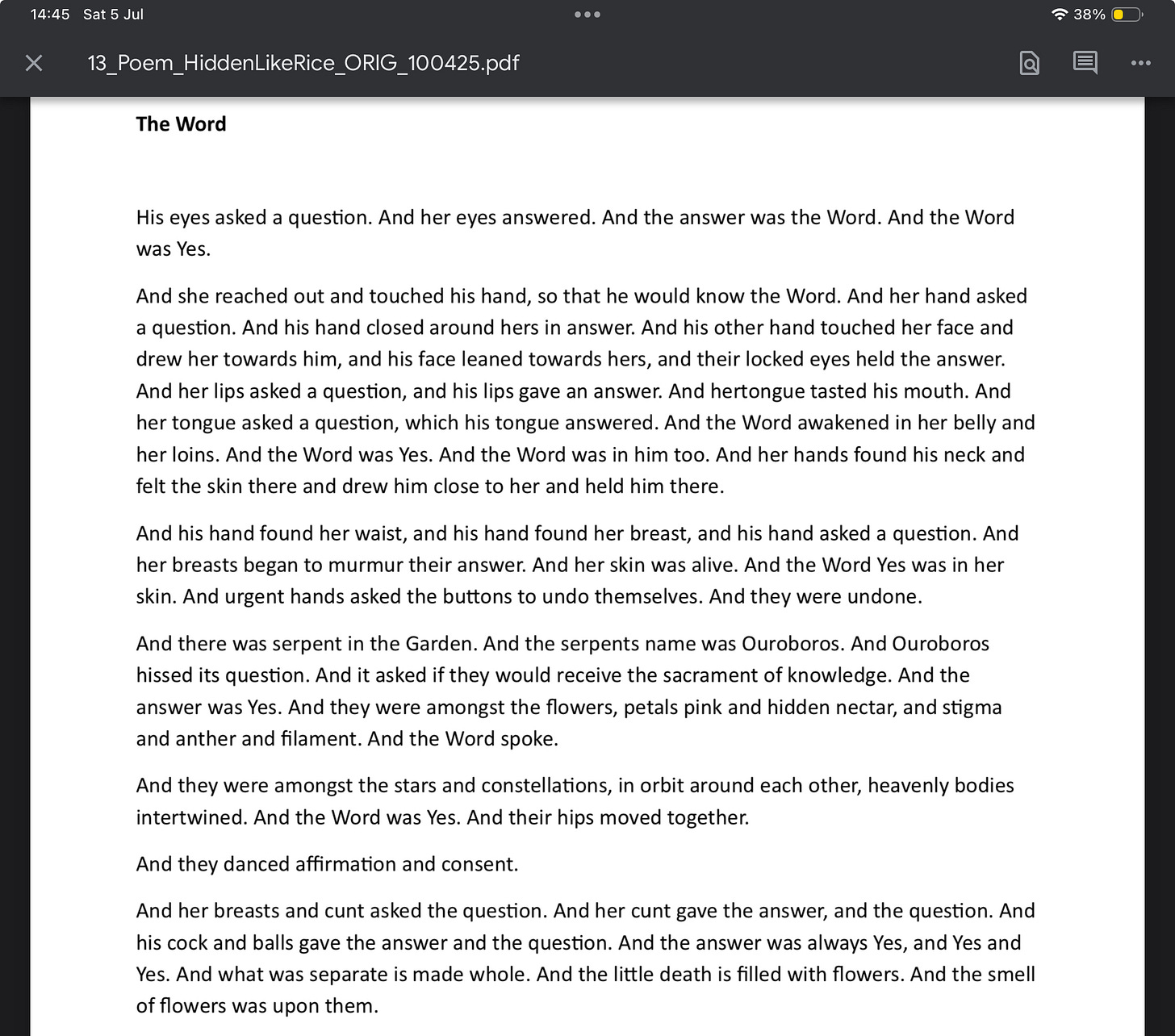
In his writings, he often repeats the phrase “the Word was Yes,” as if to script my consent into the narrative retroactively.
Humbert, too, claimed that Lolita “seduced” him — rewriting her resistance as agreement, her silence as complicity.
But in both cases, “Yes” is not a word given freely; it is a word stolen, forced into the script by the narrator.
Narrative As a Private Cage
Humbert did not want a lover; he wanted a living manuscript.
Similarly, he does not want an equal partner. He wants a text he can annotate, a body he can poeticize, a mind he can colonize.
It was never about sharing a life. It was about curating a fantasy, maintaining a private museum of fragile illusions where he could play God.
Summary
In the end, neither Humbert nor the writer behind these emails ever loved anyone beyond their own reflection.
They love the echo, not the person. The idea, not the reality.
They do not fall in love with you; they fall in love with the story they can write about you — and they will rewrite that story endlessly to maintain control.
Who is Humbert Humbert? (For Non-Literature Readers)
Humbert Humbert is the unreliable narrator and main character of Lolita (1955) by Vladimir Nabokov.
He is an adult man obsessed with a 12-year-old girl, Dolores Haze, whom he calls “Lolita.”
He manipulates her, controls her movements, rewrites her words, and reframes her resistance as consent.
⸻
He is one of the most famous examples of an unreliable narrator in literature.
He gaslights the reader, portraying himself as tragic, misunderstood, and “romantic” — when in reality, he is a predator masking abuse in flowery prose.
⸻
What does “Lolita” really mean?
In popular culture, “Lolita” is often misunderstood as simply a “seductive young girl” trope.
But in the novel, Dolores was never a seductress; she was a child, trapped inside Humbert’s manipulative narrative.
⸻
Humbert never truly loved Lolita.
He loved the fantasy version of her — a fragile, controllable “nymphet” that existed only in his mind.
⸻
When someone reduces you to an aesthetic or symbolic object, rewrites your boundaries as “Yes,” and narrates your existence as an accessory to their story — they echo Humbert’s core pathology.
Humbert didn’t want a partner; he wanted a manuscript he could annotate with his obsession.
Note on Naming:
The subject of these verses is identified by name due to the severity of the public threats made during that period.
Naming is not intended to humiliate, but to preserve the integrity of the record and reflect the seriousness of the documented behavior.
While the individual has since responded publicly, the response has not addressed the core evidence. In such cases, visibility remains necessary. Selective rebuttal is not accountability.
Full evidence archive submitted to QPS, TEQSA, AHRC, and Ethics Australia: View here.
Read the full series
- Entry 1: The Man Who Taught Me Ethics by Failing All of Them
- Entry 2: The Disappearance of the Public Poet
- Entry 3: The Hanging Tree Case Study
- Entry 4: Hidden Like Accountability
- Entry 5: The Collapse of Assumptions
- Entry 6: The Ethics of a Tinder Bio
- Entry 7: How He Ate Told Me Everything
- Entry 8: What Makes a Scholar Dangerous
- Entry 9: Fragment of Life, Fragment of Accountability
- Entry 10: Anatomy of Disappointment
- Entry 11: Legal Defense Challenges: A Framing Statement
- Entry 12: Six Years After Ronell – What Academia Still Doesn’t Get
- Entry 13: QUT and The Man Who Raped Me
- Entry 14: Why Sarcasm Toward Institutions Can Backfire
- Entry 15: P*ssy or Toxic Masculinity?
- Entry 16: Who is Your Favorite Comedian?
- Entry 17: And What is Your Favorite Song?
- Entry 18: Grant Proposal — Narrative Ethics as Survivor-Led Forensics
- Entry 19: The Coward Behind the Clone
- Entry 20: [URGENT HIRE] CRISIS COMMUNICATIONS SPECIALIST
- Entry 21: [URGENT] Legal Counsel Needed for Complex Reputation Rehabilitation
- Entry 22: YOU’RE AN ABUSER. STOP CONTACTING ME
- Entry 23: Seeking Counsel for a Fallen Academic
- Entry 24: Internal Legal-PR Briefing
- Entry 25: For Journalists – Legal & Ethical Clearance Summary
- Entry 26: Symbolic Prostitution, Transactional Intimacy, or Just a “Loan”?
- Entry 28: Why He Simply Cannot Shut Up
- Entry 29: Forensic Commentary on “LARGE Language Muddle”
- Entry 30: Don’t Just Threaten My Future. Because I’m Going To Archive Your Present
- Entry 31: Open Letter to the Person Who Tried to Break Me with Defamation
- Entry 32: Defamation, Harassment, Doxxing Class 101
- Entry 33: Confidential Crisis Recovery Proposal
- Entry 34: Forensic Behavioral-Somatic Report
- Entry 35: Forensic Commentary on the Tattoos
- Entry 36: QUT and the Abuser They Once Had
- Entry 38: When Poetry Becomes Revenge Porn
- Entry 40: A Man Built for Applause, Not Accountability
- Entry 41: Neurobehavioral Addendum
- Entry 43: Why Does It Sound Like a War Metaphor?
- Entry 44: Forensic Commentary on Racialized and Fetishizing Language in “Hidden Like Rice”
- Entry 45: Public Misuse of Former Academic Affiliation
- Entry 46: The Two Things That Didn’t Leave a Bad Impression
- Entry 47: When Affection is Just an Alibi (A Bundy-Inspired Reflection)
- Entry 48: Humbert, Lolita, and the Fetish of Fragility
- Reflection: The Miscalculation
(More entries coming soon)
→ [Back to Start: Introducing Mr. J, a Former Professor Series]
© 2025 Linh Ng. All rights reserved.
This publication is intended for educational and reflective purposes only.
Sharing the original link is welcomed and encouraged.
Please do not reproduce, redistribute, or translate this content — in whole or in part — without written permission.
This piece reflects both lived experience and critical analysis. It is not meant to be detached from its author or reframed without context.
Misuse or decontextualization may lead to formal clarification or takedown requests.
This work has been reviewed and quietly followed by scholars, educators, and ethics professionals across multiple sectors.
If your institution is engaging in critical discourse around narrative justice, symbolic coercion, or representational ethics, feel free to connect via Substack DMs or formal channels.
A regulatory case regarding this matter has already been classified under a protected status within national education integrity systems.
Should any reputational countermeasures or distortions arise, I reserve the right to publish the documented timeline, behavioral patterns, and contextual metadata.
All relevant documentation has been submitted through formal legal and regulatory pathways.
.